Trend Micro explains the trends of internet fraud rampant in Japan
In response to the growing threat of internet fraud in Japan, Trend Micro held a seminar on fraud trends on the 16th (Wednesday).
Last year, we often heard about romance fraud and SNS-type investment fraud, but basically, fraud via the internet or telephone is rampant. A recent trend is that not only individuals but also corporations are becoming victims.
Motono Kenichiro, chief fraud analyst at Trend Micro, said, “We have set up research centers around the world to monitor underground trends in cybercrime in each region. It is often the case that fraud methods that are rampant in the underground overseas are confirmed in Japan several years later.”
There have also been confirmed cases of cybercrime groups believed to have bases overseas targeting Japanese people and Japanese organizations to commit fraud.
One domestic fraud trend that deserves attention is phishing fraud. A typical example is a phishing site that steals credit card information. Not only do they impersonate credit card companies, but there is also an increase in those that impersonate overdue utility bills.
“Credit card information obtained on phishing sites is not just used as is. Criminals may collect and list card information and sell it on Telegram and other platforms. We have confirmed several Telegram channels selling Japanese people’s credit card information,” said Motono.
Recently, phishing sites targeting crypto assets have also appeared. The company has confirmed cases where users were led to a fake National Tax Agency website in an attempt to steal crypto assets.
Phishing sites do not only target financial assets. There are also phishing sites circulating that steal images and information of personal identification such as driver’s licenses, passports, and My Number cards. Stolen personal identification information is then misused in other frauds. A typical example is “SIM swaps,” which reissue SIM cards. A service that illegally creates SIM cards has also been confirmed on Telegram.
According to the company, there are criminal groups that mainly target city banks, and criminal groups that target small and medium-sized financial institutions such as online banks, regional banks, and trust banks.
Financial institutions have introduced two-factor authentication such as one-time passwords to counter phishing sites, but real-time phishing that breaks through these is now rampant. In recent cases, there have been a series of reports of securities company customers being forced to buy Chinese stocks without their intention.
“According to our research, as of March this year, at least 10 phishing kits were used on nine securities companies. We suspect that multiple fraud groups are setting up phishing sites for securities companies,” says Motono.
The criminal group sends a message of high urgency to the securities company’s customers. From there, the user is transferred to a login screen where the login ID and password are stolen. After logging in, a form to obtain personal information, including the transaction PIN, appears on the screen. It seems that criminals are stealing this information to illegally purchase stocks.
The damage caused by phishing scams to corporations is also becoming more noticeable. For example, there was a sharp increase in suspicious phone calls pretending to be from banks from February to March this year. This method involves calling companies pretending to be banks, obtaining their email addresses, and then sending phishing emails. These phishing sites are designed to require users to enter contact phone numbers and preferred contact times, so they are thought to be searching for new corporate targets.
Smishing, a type of fraud using SMS, is also on the rise. The most common method is to send fake message links via SMS and get users to click on them to steal personal information or infect users with malware.
According to the company, two types of malware are spreading in Japan as a result of smishing. The first is “XLOADER,” which has been active since around 2019. Once infected, the attacker remotely controls the user’s device to send SMS messages.
“Recently, they have been actively distributing SMS messages purporting to be from banks, directing users to bank phishing sites,” said Motono.
The second is “KeepSpy,” which has been active since 2021. Many of them are disguised as security software from major mobile carriers. Once infected, the attacker remotely controls the user’s device to send SMS messages. SMS messages purporting to be from regional banks are now being launched as part of a campaign.
Smishing applies to the next-generation messaging standard “RSC,” which was developed as an evolution of SMS.
“In fact, since April last year, there have been cases where the group chat function of RCS has been abused. At first, it was only for Android, but it has now been applied to iPhones as well. We fear that fraud using RCS will spread in the future. Unlike conventional SMS, RCS contains a lot of information, so we think that it will come to the surface all at once,” explains Motono.
Support fraud is also rampant. This type of fraud has been on the rise since 2022, where fraudsters pretend to be fake technical support, send warnings to users’ computers, and lead them to fake support hotline phone numbers, where they cheat out of paid support fees. It has been expanding since 2010. Many of the routes that support fraudsters take are online advertisements placed on legitimate sites.
“A long time ago, avoiding advertisements on suspicious sites was the basic measure to protect yourself from online fraud, but nowadays, simply avoiding advertisements on suspicious sites is not enough,” says Motono.
Support fraud methods are also becoming more malicious. For example, they trick users into installing ScreenConnect, a remote control tool. The criminals remotely install Lock My PC, a screen locking tool, and make the user unable to use the computer. In other words, they make the user infected with ransomware. Support scams target not only PCs, but also mobile devices.
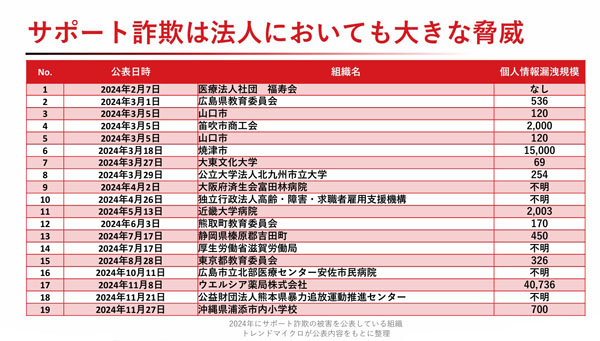
“In fact, support scams are increasingly targeting corporations. Last year, local governments, hospitals, and educational institutions were the main victims,” said Motono.
When you fall victim to a support scam, your computer is remotely controlled, and your personal and confidential information is stolen. There have been cases where tens of thousands of pieces of personal information have been leaked, making it a major threat to corporations.
Motono said, “You need to be aware that if you use the Internet, you will be scammed. It is becoming increasingly difficult to avoid scams.” He added, “Criminals use information that has already been leaked to launch scams, so it is effective to prepare yourself in advance by knowing how much information about you and your family has been leaked.”
※Translating Japanese articles into English with AI