Developed a cache random function that eliminates vulnerabilities when acquiring and updating data between CPU memories NTT
NTT, Tohoku University, and Ruhr University Bochum in Germany have developed a dedicated cache random function that eliminates the vulnerability caused by delay differences caused by caches when data is updated between CPU memories. This realizes a highly secure CPU that prevents information leakage due to cache attacks. Specifically, it becomes possible to eliminate malicious vulnerabilities that use contention-type cache attacks such as “Spectre” and “Meltdown.”
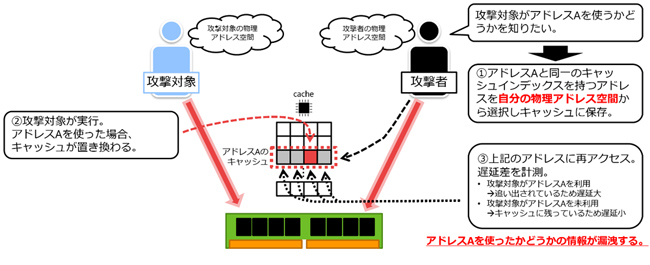
Recent CPUs introduce a cache memory to place data accessed once closer to the CPU, thereby speeding up subsequent references and reducing the effects of delays required for exchanging data between CPU memories. However, the address that has been referenced once can be referenced at high speed from the next time onwards, and can be abused by an attacker. Attacks that exploit this information are called cache attacks, and countermeasures are needed because they lead to real vulnerabilities.